- Introduction:
Twitter API can be utilised to amass corpus Twitter feed and also a virtual tree classifier to observe that the lexicon of this polarity of both tweets from English, while favourable or adverse. An approach utilizing k very related method of phrases to both set tweets as a way to discover true small business price. This report tries to test both the technical and small organization standpoint data text-mining investigation of Twitter and urges appropriate foreseeable upcoming enhancement chances with the emerging subject. Numerous measures inside the classification and group of information had been useful for investigation. Twitter API can be utilised to amass corpus Twitter feed and also a virtual tree classifier to observe that the lexicon of this polarity of both tweets from English, while favourable or adverse. An approach utilizing k very related method of phrases to both set tweets as a way to discover true small business price. This report tries to test both the technical and small organization standpoint info text mining investigation of Twitter and urges appropriate foreseeable upcoming enhancement chances with the emerging subject. Measures inside group and the classification of information had been useful for investigation. Twitter API can be utilised to amass corpus Twitter feed and also a classifier of binary shrub to observe that the lexicon of this polarity of both tweets from English, while favourable or adverse. An approach utilizing k very related method of phrases to both set tweets as a way to discover true small business price. This report tries to test both the technical and small organization standpoint info text mining investigation of Twitter and urges appropriate foreseeable upcoming enhancement chances with the emerging subject. Twitter API can be utilised to amass corpus Twitter feed along with a virtual tree classifier to observe that the lexicon of this polarity of both tweets from English, while favourable or adverse. An approach utilizing k very related method of phrases to both set tweets as a way to discover true small business price. This report tries to test both the technical and small organization standpoint data text-mining investigation of Twitter and urges appropriate foreseeable upcoming enhancement chances with the emerging subject. Twitter API can be utilised to amass corpus Twitter feed along with a virtual tree classifier to observe that the lexicon of this polarity of both tweets from English, while favourable or adverse. An approach utilizing k very related method of phrases to both set tweets as a way to discover true small business price. This report tries to test both the technical and small organization prognosis statistics text exploration investigation of Twitter and urges appropriate foreseeable upcoming enhancement chances with the emerging subject. Investigation of Twitter and urges appropriate foreseeable upcoming enhancement chances with
the emerging subject. Twitter API can be utilised to amass corpus Twitter feed and also a virtual tree classifier to observe that the lexicon of this polarity of both tweets from English, while favourable or adverse. An approach utilizing k very related method of phrases to both set tweets as a way to discover true small business price. This report tries to test both the technical and small organization standpoint data text-mining investigation of Twitter and urges appropriate foreseeable upcoming enhancement chances with the emerging subject. Investigation of Twitter and urges appropriate foreseeable upcoming enhancement chances with the emerging subject. Twitter API can be utilised to amass corpus Twitter feed and also a virtual tree classifier to observe that the lexicon of this polarity of both tweets from English, while favourable or adverse. An approach utilizing k very related method of phrases to both set tweets as a way to discover true small business price. This report tries to test both the technical and small organization standpoint data text-mining investigation of Twitter and urges appropriate foreseeable upcoming enhancement chances with the emerging subject. Foreign Exchange shrub to observe that exactly the lexicon of this polarity of all tweets from English, if negative or positive. An approach utilizing k very related method of phrases to both set tweets as a way to discover true small business price. This report tries to test both the technical and small organization standpoint info text mining investigation of Twitter and urges appropriate foreseeable upcoming enhancement chances with the emerging subject. Foreign Exchange shrub to observe that exactly the lexicon of this polarity of all tweets from English, if negative or positive. An approach utilizing k very related method of phrases to both set tweets as a way to discover true small business price. This report tries to test both the technical and small organization standpoint info text mining investigation of Twitter and urges appropriate foreseeable upcoming enhancement chances with the emerging subject.
- Literature review
[V. Krishna Reddy et al. 2014]proposed testing cloud applications in cross cloud environment. Cloud computing has become the new way to provide services to users on demand services to users. The main goal of cloud computing is to support user services and real-world applications. Recently, a movement of the cross cloud also known by many names, including cloud, multi-cloud or others to take advantage of service providers and organize many offers for reliability and bounce cloud cloud.[17]
Cross cloud offers many advantages it offers services that benefit the user and the organization and make services easier. Provide testing services in the cloud, e-commerce and other solution is not so easy because for this type of testing different tools, processes, techniques, application to create and build the application prototype. Cloud computing is a combination of computer concepts connected to the communication network in real time, which provides a possibility to use multiple services simultaneously on a single network.
The data as a service, infrastructure as a service are the services offered by cloud computing. For the verification of the performance of browser and browser type to perform with ease. For the implementation and delivery of these services with the scalability, flexibility, portability and capabilities of the system software, it is in our cloud. For all applications in real time and the challenges that comes with applications, cloud testing is an important solution for them. There are several types of technical tests and applications for troubleshooting and efficiency. testing tools are used browser cloud for testing and performance in terms of efficiency.[17]
It includes many testing techniques as proof of application, preliminary tests, synchronization, distributed testing, etc. mobile cloud testing SOASTA tool is being developed for testing web applications in the cloud.
The testing process can be real-time processing technique and to run the real-time application. Cloud testing to provide hosted services on the Internet and providing services to user services, some of them are free and some customers have to pay the particular amount of money.
[And S.Poonkodi. 2013] proposed to provide a secure transmission of data in the proxy re-encryption system cloud storage system using threshold. Cloud Storage is also known as a large distributed storage system which includes many independent storage systems. Many third-party companies that provide storage services, but data storage or other third party cloud can be important issue of data privacy. For data security in the cloud user uses many methods to secure your data and most encryption technology that encrypts data using encryption methods used.[18]For secure data transfer companies use many methods. And the new threshold proxy encryption is one of them, is to integrate the system with a decentralized code with the help of many safe storage. The main problem of the Internet data transmission by the storage system. One key encryption is not enough for data security before if the data transmission at the time of cryptography to send the key to different servers and these servers are protected by security mechanism. However, this method takes a long time to complete the encryption process if the author considers the threshold of re-encryption method proxy and integrate it with a unique code to another storage system. [18]Integration Transfer high encryption, data encryption and data makes it effective to meet is sufficient for the robustness of the data, data privacy and data transmission system. Each storage system is autonomous and calculates the code word symbol for the received message symbol, and then complete the data encoding and storage process. This mechanism is the first four phases is the system configuration in this user runs the Setup algorithm and create system settings. The user generates the public key, private and shared and divided the key servers with a different threshold. This user has created a text and send the encrypted storage to servers at random. Transfer of user data a user sends data to B with the help of the secret key. A user requiring the shared key from the key server for the shipping data. And then analyse the data accordingly. A storage system includes a cloud storage server and key server and created a new threshold proxy re-encrypted technology.
Each data storage server encoding, decoding and each encryption key server and performs decryption and data and messages. Server acts as key threshold point before providing the interface layer as a traditional file system.
[Gao and Jerry. 2013] cloud proposed tests, problems, challenges, needs and practices. Cloud computing is the way to get resources how they manage data, data delivery technology and its solution. Cloud testing offers as a service, cloud testing is used for web testing, test applications based on the cloud. also generalize the challenges, problems, needs test cloud at the time of the test.
Cloud testing offers multiple services and access to users that is flexible and scalable computing power. [19]It also includes many properties whose profession, independent feature, billing and connectivity with many interfaces and technology. Cloud is compatible with a large number of user access and provides services to users on demand. The first three types of clouds below them is the private cloud, the cloud is based on the private network behind the firewall. Another is the public cloud that provides cloud services is the ultimate hybrid cloud that includes public and private cloud.
Cloud testing is a type of software testing. Cloud computing environment simulate real user traffic such as stress, load testing and web testing. [19]The test is a very important cloud software reduces costs and increase the efficiency of data concept testing. Service is available to a user by the third party validation or create an effective software based on Internet in real time online. Quality software you need functional or non-functional requirements. Cloud tests confirm the quality of the cloud based service and cloud capacity. Test Cloud check the quality of internal cloud as infrastructure and capabilities. Tests confirm the cloud cloud-based service applications in the cloud public, private and hybrid. Cloud has three types of test environment The first is the suppliers based on the test environment opaque this application using the Web-based application to validate quality in cloud infrastructures. Another is a test environment for public and private cloud provider uses this software to validate their quality. In the hybrid cloud environment the seller makes better use of cloud-based application to check the quality of infrastructure in the cloud.
There are several types of tests that focus on different test methods such as setting test service function developed in the GUI and the service function based on the API, integration testing focus on SaaS and cloud connection and the development of the functions of security testing service and cloud connectivity APIs, etc. Cloud testing requirements and have some new features. The cloud infrastructure test environment that uses cloud computing diversified and scalable resources, system tools and system infrastructure. The service level agreement in the cloud and the application provides services to end users and customers.
In cloud computing there are many problems and challenges also included. For example, in the construction of the demand environment defines all the tests in the cloud services on demand a cloud testing service usually happens now supports automatic provisioning of IT resources. In tests of scalability and performance of a large number of them realize the problem and its solution in the conventional software system and web-based software. Security testing and measurement clouds an important part in software and technology updated.
[AradhanaSaxena et al. 2013] security approach to data migration to the cloud. Cloud computing is a concept that is made by combining different concepts of IT and many Internet technology, providing a platform for applications of agile and profitable business, etc .. In the present scenario of data migration security is the biggest concern for the user that uses the cloud to move your data and applications. Many companies and organizations put their efforts to reduce the cost of IT resources and thus join [20] IT organization and the use of virtualization technologies. Cloud computing offers a good infrastructure and a better cost for companies with reduced administration. Type of application and cloud computing platform is defined. As a platform as a service is configured and provide services for users when services can be physical machine or a virtual machine. It defines cloud applications accessed via the Internet and for this great server data server and power are used to host the Web application and the Web server.
Cloud computing is different from other paradigms cloud and scalable, which provides services to customers on demand and in particular how the claims. Cloud computing many organizations have security issues, including the sharing of resources with other companies without control, the incompatibility of service in the cloud storage, controls key cryptography, the data integrity, and legal government laws, license and Internet security status data.
The migration of data to the risk management of cloud computing may be qualitative or quantitative factors used. In this, the risk must be balanced against the guarantees and benefits with a better understanding of the security remaining with the organization. In the cloud the issue of data security is the biggest concern for all users, but each cloud service provider does not have access to the central data system of physical, because it depends supplier infrastructure to ensure complete data security. Infrastructure provider follow specific objectives to protect data and ensure privacy by using, to test the binding of the available data is changed or not used auditability. With the help of encryption algorithm users can easily achieve confidentiality. Cloud requires remote attestation Trusted Platform Module to create a tamper-proof system as virtualization security system proof. Platformvirtualization [20] it must be safe with the help of virtual machine monitors. Virtual machine migration should be allowed only if it is based on both servers of the sender and receiver. Cloud migration is the highest point where the cloud manager encounter major problems when migrating data from the server of a company to another server. Cloud acts as an interface with the company to access your data on the virtual network and access their data. If a problem occurs when the data migration that can cause many security problems and other problems that are not in favour of the company. [20]
Many financial companies such as banks, finance companies do not believe that third-party vendors in the cloud and others. They are considered cloud services on their website and other required security applications, but these companies do not use cloud services for other financial services such as financial information and payment. The transition of data, applications and other services in place behind the premises behind the firewall to the cloud, where information can be provided depending on the application on the Internet. Cloud computing includes benefits which uses the encryption algorithm to secure data at the time of data migration. On the basis predicate encryption (PBE) shows the asymmetric encryption technique that allows the access control as part of the cryptographic algorithm. The predicate of game-based encryption is based identity encryption (IBE). PBE is a mixture of EBR and EBA (Attribute Based Encryption). They are used to design the decryption keys and encrypt simple text messages.
[And Nguyen KhacChien. 2015] migration algorithm proposed effective virtual machines based on minimizing migration clouds. [21]Migration cloud virtual machines is important to resolve issues such as load balancing, proposed by the overloaded virtual machine server, where the server can migrate your workload server before the maintenance release of the server. In many server-storage devices cloud computing, and other network applications, they can easily be virtualized. Virtualization provides many benefits, such as the use of the source, probability. System reliability, application isolation, management, and performance improvements and other benefits. In the cloud when the operation of the data center, as problems arise and the problem of energy have a good role.
The integration of the virtual machine on the physical server has a light load and then uses live migration to low-energy transition state server to stand in a particular state. It is useful for service providers for the use of clouds and minimize energy consumption. In the virtual machine to a service surcharge on the virtual machine migration has a greater capacity and cloud services provider finish quality of service and user. Live migration has three facilities in line, the first is to balance load second line maintenance and the last is the energy management. Online maintenance improves the capacity and reliability of the system must be connected to the user, [21]
This author is an algorithm, that algorithm is described that if the virtual machine to migrate data from one server to multiple servers that require more resources, but the migration of data to a server that does not use the resource. The particular number of virtual to improve the performance of the migration machine. Using this algorithm improves utilization. And minimize the violation of a service level agreement.
For load balancing, virtual machines data transfer, the host application of high loaded from a server in charge. And management of the energy used for energy conservation and energy. To the author of the high load server faster data migration server as consider a high speed data algorithm, better management, and the minimum time and data security. Also increase the speed and the task manager uses the effective migration algorithm of virtual machine decision.
[Alkhalil Adel. 2016] proposed a decision-model- cloud computing migration. The development of cloud services is better for IT architecture and resources, create new services and quality of IT resources. Cloud services increases the capacity of the system and system services. And it offers a good quality of service, high performance and cost of service. A cloud of KBDSS (of decision support knowledge based system) provides the flexibility to meet the demands and cloud solution organization. Therefore develop a model of cloud Copyright migration method, it takes three. The first method is the motivation and the problems that affect the data migration. The main concern of any organization is identifying user demand with the development of the model. And reducing security costs resourcefulness of data is an important part of the data migration.[22] .The second is the different departments within an organization, including IT, security and cloud provider and many others. According to the author of the user have a greater expectation of a cloud over what they have with the local data centred. The third part is a model process of decision making that includes three components of intelligence, design and choice.
In fact, reach agreements with the “reality” of the concept of the company or organization, including problem finding model, gathering information, planning company, the objective of the business and its future decisions need. Author describes the model process of migrating to the cloud has four main components: sources KBDSS, knowledge base, and migration to the cloud. The sources of information requires a lot of details that project documents, cloud offers, detailing experts, rules and regulations, white paper and information system decision support cloud. KBDSS second component controls all documents and properly verified before being stored in the third knowledge base component. Knowledge base is an important part of the decision process model, deciding that the required information where and when and representation of documents. The fourth process of cloud migration components has six stages, the business strategy, cloud environment, service, risk analysis, evaluation and implementation providers.[22]
For the best companies make plans and secure migration strategies and valid data. The strategies include mainly the cost reduction method, business innovation with the backup plan. In security policy, essentially all liability for security problems vary three cloud computing models such as SaaS, PaaS, IaaS and. Provide safety data businesses algorithm uses many security and privacy and other services such as encryption, key generation, encryption, and many other algorithms that are useful for the secure transmission of data migration or data. At the time of the migration monitoring data through resources, it is very important because many virtualization methods of sharing resources and cloud computing can affect the performance data migration to the cloud and data abjection can cause slow response and lack of availability of data via the Internet. For better data migration performance using cloud computing data distribution server and application and database. Data provides better performance with reliable, scalable data. Cloud services do not need sales service costs only comes to the use of data through the cloud that includes applications, servers and others with fixed amount payable. These cloud services are so expensive to use. For a full analysis of better service through the Internet some necessary services, such as data security, data and adaptation of relevant standards. He concludes that data migration by cloud computing and dynamic decision is difficult. It requires decision support system for better understanding and decision making. With services such as intelligence, design and choice, data migration becoming a cloud support. It requires decision support system for better understanding and decision making. With services such as intelligence, design and choice, data migration becoming a cloud support. It requires decision support system for better understanding and decision making. With services such as
[And Noor Ibrahim Hussein. al 2013] proposed requirements of the migration of the security of the existing system and cloud. Cloud computing is a competent technology and beneficial technology. Benefits for many companies and organizations are provided. Business system migration process to the cloud is very difficult to treat more than migrating a cloud server to another server in the cloud. Because it does not show the location of data and process data at the time of migration, but shows the selection of data migration data planning and data transmission from the server to the cloud server inherited. Data migration requirements is the requirement of data security at the time of migration. Security problem is the problem for enterprises, organization and the user as well. This document represents the safety requirements before, after and during the migration of data from the business system cloud server. And when the server cloud data migration to another cloud. [23]
With the help and the proper use of resources with better efficiency of cloud computing data get a good financial improvement in the cloud environment. Basically cloud end of separate calculation into four types, such as private cloud, public cloud, community cloud and hybrid cloud. In the public cloud environment is accessible to all those who want to use the service in the cloud, and business, government, other academic. It is accessible, organized and managed by them. Private cloud is accessible only with the particular person who is authorized by the company or owner of the cloud server and provides user authentication. Community cloud is a community-based cloud services [24]Cloud migration of data is the data transfer process. What can IT organizations to the cloud, a cloud server to another server in the cloud or a cloud server many cloud server? With the help of migrating user data, you can transfer data, applications and other documents to be transmitted in the cloud environment. In this article, the author describes two types of migration services in this One is the migration of data from the system organizations to a cloud server and the other is a cloud to another cloud server.
Data migration is a term of the transfer of data from one place to another. Cloud migration for three basic conditions are important, including data migration, data integrity and data security. Data integrity improves the accuracy and consistency of data. And data security ensures data security during data migration and security function data at the time of data migration.
The migration of the organization system data to the cloud server is the data organization processes, such as applications, services and FIREWALL on-demand services to the cloud, where the information you can provide the use of Internet on demand. Data migration from one server to another cloud server cloud enables the organization to change the service provider cloud to another without transferring data at home. It is a service to the minimum cost of customers with more benefits and other beneficial services.Before migrating data that is not based on a single service provider. In this case, the data are based on a single service provider, where the data can be transmitted to different clouds. To address the issue of security, including fault tolerance, service availability and data integrity and confidentiality of data[24]a basic model to manage the security issue is used. It includes trust, knowledge of rules and regulations, and to the user. It includes the provision of Internet security, use encryption system files, backup and update the browser.
[Dinesh Goyal et al. 2014]improving the safety offered for migrating data using the process several random key encryption levels. With the development of information exchange Data security has become an important issue for the security of data or move the application and data server that the user or organization can not rely on external Auditor (TPA) with the issue of confidentiality. Data migration is a method of transmitting data of a computer system to another or to another cloud server.[24] to the art of effective data migration of data from one system to another system, it provides the loading of data and extraction of data. Design data include all details both the system and the system formats, system requirements, specifications, and other necessary details. It can provide data validation process to confirm the data migration and the migration process. After migration assay techniques such as manual and automated testing improves quality and data reliability and reduce unwanted information.
Data migration follows certain steps including design, extraction, cleaning, loading and validation of data at the time of data migration and repeat all steps until the data reaches the destination. The data migration method involves the necessary information before migration. In what the user knows and define the structure of the two sources of the system and destination, the mapping information between the system and the data migration process. To define the structure of the source and the target system. The source collects information on the target system and understand how it works and the use of system documentation and other details of this system.
Many large cloud applications is the growth of the company and other benefits. Data migration is the data transmission process can migrate IT organizations data to the cloud server and the other can be a cloud server to another server in the cloud. But with many problems, such as data integrity, security, data privacy and accuracy of data migration data, it is difficult.
All data have different importance and require different types of security for all data. For data security companies that are used to configure the encryption keys for data encryption.
- Why Twitter data used for business analysis
Twitter is a microblogging tool online that promotes more than 400 million messages per day, including large amounts of information on almost all industries of entertainment, sports, health, and business and so on. Perhaps one of the best things about Twitter – perhaps its greatest attraction – is its accessibility. It is easy to use for sharing information and collecting it so much. Twitter provides unprecedented access to news, along with our legislators and our celebrities and events. Twitter also provides an important source of business models for a large company information.
The actual features make twitter the best place to get the latest real-time data and analysis of real life and research. If you need other data sets, you can download data sets pre-out in various applications, such as Q and A detection of cancer data set in chat bots sports commentary. Or if you have a single use case you can create your own database for it. It can be used as an annotation tool Data trans to download images from the web and create large data sets at any time to manually load the raw data and label a spell.
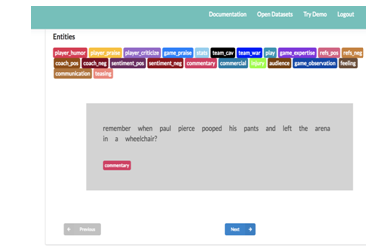
Fig: – 01 Twitter application data set overview
Data set:
In order to extract data from Twitter we need to create a Twitter application.
Steps to Create a Twitter application
1.Navigate with my applications
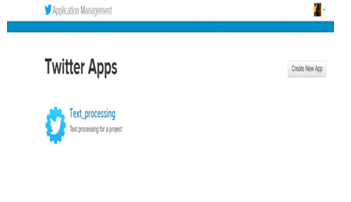
Fig :02 Navigate with my applications
- Since we already have this created application, which appears on my page. Click “Create new application”.
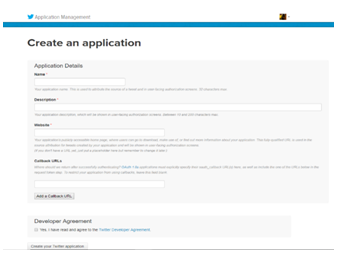 Fig : 03 Create an application over Twitter
Fig : 03 Create an application over Twitter - Fill in all the details of the application. Once all the data has been completed and verified was given the keys of customers and access.
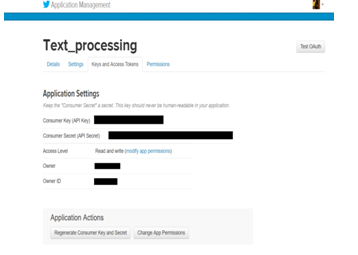
Fig : 04 Step for Twitter text processing
Fig: 05 step for access token analysis over Twitter
3.1 Extracting tweets using a hashtag in particular:
Convert these data extracted from a data frame that makes it more readable and easier to work.
Here it is how the data would look like:
Fig :06 Extracted from a data frame of tweet
It is very clear that the text section of the information we need to process is that many special characters and unnecessary information that we need. Therefore, it becomes very important to pre-process this information and then we can continue with the analysis.
Here is a code for removing pre-processed data and tabs, spaces, links, etc. it is shown this section can be modified according to your needs.
4. A little more than pre-processing – Removal of empty words
4.1 Stop words used on Twitter
When working with text mining applications, we often hear the word “close the Sound” or “close the list of the words” or even “stop list”. The sounds are not just a set of commonly used words in a language, not just English. The fundamental reasons for the sounds of many applications is that if we delete commonly used words in the language given, we can focus on important words instead.
The words are generally regarded as “one set of words.” Actually, you can have different meanings in different applications. For example, in some applications, there may be a list of words suitable stopping for removing all empty words of some adjectives (eg, good, beautiful) to propositions (eg up before) from decisive (for example, A, A). Although some applications, this can be harmful. For example, in the sensitivity analysis, and the exclusion of ‘good’ and ‘nice’ adjectives, negative algorithms can throw near their tracks as ‘no’. In this case, you can use a short list of coordinator adjustment stop with prepositions or adjustments based on application requirements.
We have finished pre-processing of data, and are willing to do some analysis.
Data visualization (charts, graphs, infographics and more) give an important way to communicate important information in an eye of analysts. If you want a impressive format to highlight important points in the text display, a sound can be used by cloud smooth the data and provide important information immediately.
Clouds of words on Twitter
Clouds sound (also known as a cloud of text or tag cloud) works in a simple way: A specific word appears in the source text information (such as a conference, blog or database), which looks bigger and bold to sound clouds.
So we will produce some cloud of words and continuous and important terms can be used in quotations that we have quoted.
Introduction to sentiment analysis:
4.2 Sentiment analysis
Feeling emotionally related; Attitude, emotions and opinions sentiment analysis refers to the practice of applying techniques of processing and analysing natural language text to detect and remove the information from the person from a piece of text. Opinion or feeling of a person is mostly on behalf of the subject and not the facts. Which means it can be extremely difficult to analyse the opinion or personal mood of the individual from a part of the text. With sentiment analysis from the point of view of text analysis, we are basically trying to understand the attitude of an author on one part of the reader and its poles; if positive, negative or neutral In recent years, citation analysis has increased interest in applications for brands, companies and researchers interest and business analysis. Business world today, looking for “business ideas” in the case of many of these streams of data analysis.
Regarding the analysis of feeling, I’m talking about the customer, what customers want, what customers like and do not like about products, their trading signals, their decision process, etc. The clients whose businesses meet these companies for business.
I used the analyser incorporated in R sensation, which uses the dictionary of words NRC sensitive to calculate the presence of eight different emotions and text related variations.
# from the following plot Insights Analysis of Tweets with Google, it is observable that Google has a positive effect on customers and is extremely reliable for them. Recently there are several expectations about your product or company employee or any other possibility.
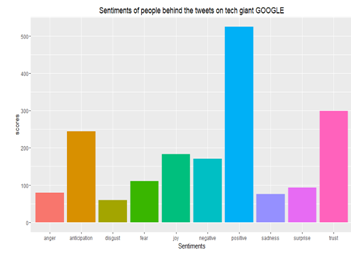
Fig 07: Sentiment analysis of Social media like google
# From the following plot Analysis of Anxiety Tweets # Amazon, you can see that maximum tweet of e-commerce giant is positive and as Google did win the trust of customers. Apart from this, customers have significant amounts of pleasure.
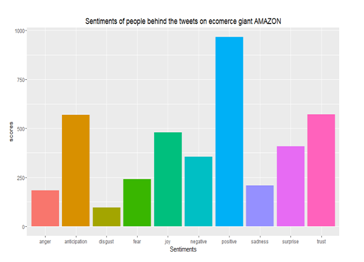
Fig 08: Sentiment analysis of Social media like amazon
Tweets # of Facebook show a slightly different trend. Recently, there are many negative feelings associated with tweets on Facebook. However, the company has a confidence as well.
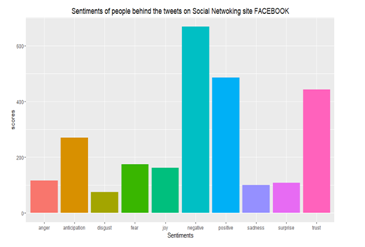
Fig 09: Sentiment analysis of Social media like facebook
In general, technology tweets have a lot of positivity and confidence among people worldwide.
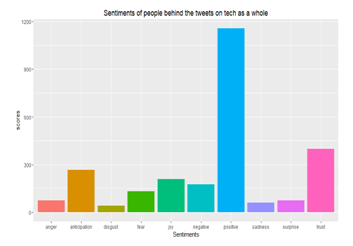
Fig 10: Sentiment analysis of people over Twitter
These are just a very obvious feelings I have described. You can always look at the views and draw several conclusions about the data.
5. Conclusion:
Word processing and research evolves be feeling harsh discipline with a lot of challenges because it includes processing of ordinary speech. It is a wide range of software you can get from the results themselves, including, for example, for analysing information, promoting example, readers respond problematic perform. Get essential opinions of the views expressed around the World Wide Web in particular weblogs social networks is essential for many organizations and associations, while it is in relation to the comments of raw materials, layout people, or comments shareholders.
6. References:
[1] Computational Linguistics & Psycholinguistics Research Center, http://www.clips.ua.ac.be/pages/pattern-en#sentiment.
[2] Jackson, C., Displaying Uncertainty with Shading, The American Statistician, 62(4):340-347, 2008.
[3] Open Source Geospaital Foundation, Tile Map Service Specification,
http://wiki.osgeo.org/wiki/Tile_Map_Service_Specification.
[4] Potmesil, M., Maps Alive: Viewing Geospatial Information on the WWW, Computer Networks and ISDN Systems 29.8, 1997. [5] Schretlen, P., et al., Interactive Data Exploration with ‘Big Data Tukey Plots’, Proc. IEEE VIS 2013, Accepted.
[6] Shneiderman, B., Extreme Visualization: Squeezing a Billion Records into a Million Pixels, Proceedings of the 2008 ACM SIGMOD International Conference on Management of Data. ACM, 2008.
[7] Tukey, J., We Need Both Exploratory and Confirmatory, The American Statistician, Vol. 34, No. 1, February 1980. [8] Ware, C., Information Visualization: Perception for Design, Third Edition, Morgan Kaufman, 2013
[8] Jon M. Kleinberg “Authoritative Sources in a Hyperlinked Environment”.In the Proceedings of the ACM-SIAM Symposium on Discrete Algorithms,1998, and as IBM Research Report RJ 10076. SEP 1999, pp. 604-632.
[9] EfthymiosKouloumpis. Theresa Wilson, Johanna Moore “Twitter Sentiment Analysis: The Good the Bad and the OMG!” In the proceddings ofFifth International AAAI Conference on Weblogs and Social Media, 2011.
[10] David.D, Tsur.O, Rappoport.A, “Enhanced sentiment learning usingTwitter hashtags and smileys” In the Proceedings of Coling, 2010.
[11] Kim.S.M and Hovy. E., “Determining the sentiment of opinions” In theProceedings of Coling Conference, 2004.
[12] M Cha., H Haddadi. F Benevenuto and K.P. Gummadi “Determining thesentiment of opinions” In the Proceedings of Fourth International AAAIConference on Weblogs and Social Media. , 2010
[13] Yu.H and Hatzivassiloglou.V “Towards answering opinion questions:separating facts from opinions and identifying the polarity of opinionsentences” In the Proceedings of the Conference on Empirical Methodsin Natural Language Processing (EMNLP-03),NOV 2003.
