A Novel approach for information sharing in Supply chain management
1Priti Lale,2Manish Sharma
1,2Deparment of Computer Science & Engineering, Suresh GyanVihar University Jaipur, (RJ) India.
1priti.met@gmail.com
2 manish.sharma@mygyanvihar.com
Abstract
In today’s world information plays very important role while sharing with its users. Information sharing describes the data exchange between people, various organization and technologies, in different service sectors like financial sectors, medical sectors, emergency service sector secured information sharing is mostly an important area which needs to achieve effectively. Specifically in logistics management where supply chain management and supply chain engineering which plans, controls and implements the efficient storage of goods, services, and related information between the point of origin and point of consumption to meet customer’s requirements. In this paper a novel approach for secured information sharing is discussed with block chain technology by insisting the utilization of optimization concept in the data privacy preservation via selecting the optimal key required for sanitization.
Keywords: Supply chain management, block chain technology, Information sharing.
- Introduction
Information security is at most important now a day for companies which most people still do not get it. Organizations fill that there information is secured and it can’t attract threats which is big mistake they are making.
companies work hard to takes steps to protect its intellectual property, but it is also important to not blindly believe that someone cannot break into your data. For giving assurance to organizations regarding total security of data many existing models are trying to work in this area[1][2].
InfoSec, which is also called as information security, is a process of prevention of unauthorized access, confidentiality, counter threats ,disruption, modification and destruction of business information. Information security is badly needed in companies where data is secured from the malicious purpose in the system. Digital or non-digital information can be of any form and it could be anything like your personal information, business information, confidential data on personal computer and mobile devices etc. Information sharing is crucial in many areas one such area in which paper is focused on is supply chain management[3]. Supply chain management is a process used by organizations, companies to make sure that their chain in which different stakeholders are involved is cost-effective and effective[12]. A supply chain is the combination of steps which companies, organizations takes to transform a final product from raw material. There are various stages involved in supply chain where security is the main concern as the chain contains multiple stakeholders, the stages are planning, developing, making, delivering and returning[4].
- Literature Review
Blockchain technologies largely used in the operations and logistics domain as well. Currently, supply chains are becoming more complex from logistics in structure, task are becoming difficult, and stakeholders are diverse, and many organizations do not provide an entire supply chain integrated view[11]. organizations who termed as large have built their own systems and identities for maintaining coverage of operations which are global and effective for giving power to interact with the suppliers[9][10]. Otherwise, centralized regulatory bodies or intermediaries in which they need to rely. Because of transparency issues many difficulties and problems are there in the supply chain mechanism in terms of traceability, security, verification and authentication of system. Blockchain will be excellent solution to provide the challenges of supply chains, and therefore it is good decision to adopt blockchain technology, with its features of, transparency, unchangeable and dependable, for providing more security and visibility in the logistics[5][6]. In proposed approach an advanced algorithm is discussed where by using the process of key generation the security of data is maintained at each level by using FSL no algorithm.
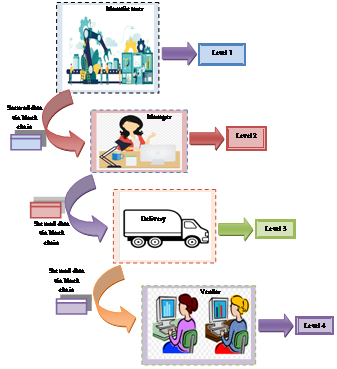
Fig. 1 Process of Supply chain management
In supply chain management there are different levels which are responsible for passing data from one end to another the levels are manufacturer, manager, delivery, and vendor. As shown in Fig.1 at manufacture end different firms create their own database with different records like Item Description, Brand, Item Quantity, Price, Weight (Kilograms), Managed By (Manger), Shipment Mode (delivery),Vendor, etc. Each manufacturer sanitizes the sensitive data and creates an individual blockchain. When the blockchain from the manufacturers reaches the mangers; the concern manger gets the likelihood to access the data block allocated to them, and further creates their blockchain. Similarity, the delivery and the vendors on acquiring the block of information from the manger and delivery creates the blockchain, respectively[7][8].
In supply chain management as each level is responsible for passing the information and adding blocks at every end where each block contained the sensitive information which is to be hidden from other stakeholders. At manufacturer level the sensitive and non sensitive fields are identified where sensitive fields are to be hidden from other users.
- Methodologies
In this paper the approach discussed is achieved through two different methodologies data sanitization and data restoration in both methods the sensitive fields information is passed using key generation.
- i) Data Sanitization
Data sanitization is the process of hiding sensitive information in a test and development database by Overwriting sensitive information with a similar type of realistic-looking but inaccurate data.
In sanitization process there are five steps to be carried out 1) sanitization using key 2)Key matrix 3) Binarization 4)Original database.
- ii) Data Restoration
A data restore is the process of copying backup data from secondary storage and restoring it to its original location or a new location. A restore is done to lose data in its original state, stolen or damaged, or to transfer data to a new location. In data restoration remaining five steps are there 1) sanitized database.2) Binarization 3) subtractor 4)Restoration 5)original database.
iii) Proposed Privacy Preservation approach
The privacy preservation approach will be conducted through different processes in which the first process is key generation and second process is designing new improved algorithm which is a novel approach.
- iv) Key Generation
Key generation comprises of solution transformation in which K is transformed into reconstructed database using khatri-rao process, K is converted into K1 using matrix dimension where is length of transaction and represents count of transaction. Here the rule hiding process is done where the sanitized database is passed to the receiver using communication channel.
- Proposed Algorithm
In this algorithm there are four different phases to be carried out 1). Pray detection and tracking 2). Attacking phase 3). Circle updating position 4). Pray Searching.
In first phase the distance between the targets pray and the sea lion is identified, the sea lion moves to a position over the target prey to get much closer to the prey. In attacking phase, the phase can also called as exploration phase where the number of iterations are identified using Dwindling encircling technique for directing towards the pray. In circle updating position the basic hunting process is executed where they start hunting from edges. Lastly the distance between favorable solution and search agent is identified. In the pray searching phase sea lions search randomly employing their whiskers and swimming zigzagging to find prey. Thus, it is done with the random values. In case is greater than one or less than negative one, this leads to force sea lions to move away from the target prey and the sea lion’ leader. Therefore, this situation obliges sea lions to search for other prey.
- Conclusion
In this paper a novel approach is discussed which after comparison with existing models provide security in traversing data from one level to another and ultimately make data secure in chain of communication.
References
[1] Zhang, Lin Hou, Jia-Nan Liu, Yang Xiang, Robert H. Deng,”CrowdBC: A Blockchain-based Decentralized Framework for Crowd sourcing”,IEEE Transactions on Parallel and Distributed Systems, 2018.
[2] Tsan-Ming Choi, Xin Wen, Xuting Sun, Sai-Ho Chung, “The mean-variance approach for global supply chain risk analysis with air logistics in the blockchain technology era”, Transportation Research Part E: Logistics and Transportation Review, Vol.127,pp.178-191,July 2019
[3] YiHe Liu, Shuang Zhang,”Information security and storage of Internet of Things based on block chains”,Future Generation Computer Systems,Vol.106,pp.296-3030,May 2020
[4] Magdalena Ramirez-Peña, Alejandro J. Sánchez Sotano, Víctor Pérez-Fernandez, Francisco J. Abad, Moises Batista,”Achieving a sustainable shipbuilding supply chain under I4.0 perspective”,Journal of Cleaner Production,in communication, 2019
[5] FENG XIONG, RUIYANG XIAO , WEI REN, RONGYUE ZHENG3, AND JIANLIN JIANG,”A Key Protection Scheme Based on Secretm Sharing for Blockchain-Based Construction Supply Chain System”,Digital Object Identifier, vol.7, August 20, 2019
[6] Aimin Yang, Yifan Li, Chenshuai Liu, Jie Li, Jiahao Wang,”Research on logistics supply chain of iron and steel enterprises based on block chain technology”,Future Generation Computer Systems, Vol.101,pp635-645, December 2019.
[7] Priti Lale,Dr.Rajesh Purohit “Secured Exchange of Information in Supply Chain Management: A Literature Review”,TEST Engineering and Management January-February 2020 ISSN: 0193-4120 Page No. 8859 – 8862
[8] PritiLale, Dr. Manish Sharma “Secured Information Sharing using Data Sanitization and restoration” International Journal of Advanced Trends in Computer Science and Engineering , Volume 9, No.5, September – October 2020.
[9] Ting Chen, Derong Wang,”Combined application of blockchain technology in fractional calculus model of supply chain financial system”,Chaos, Solitons & Fractals, in communication., 2019.
[10] V. G. Venkatesh, Kai Kang, Bill Wang, Ray Y Zhong, Abraham Zhang,”System architecture for blockchain based transparency of supply chain social sustainability”,Robotics and Computer-Integrated Manufacturing, Vol.63,June 2020.
[11] YiHe Liu, Shuang Zhang,”Information security and storage of Internet of Things based on block chains”,Future Generation Computer Systems,Vol.106,pp.296-3030,May 2020.
[12] Scott DuHadway, Steven Carnovale,Benjamin Hazen,”Understanding risk management for intentional supply chain disruptions: risk detection, risk mitigation, and risk recovery”Ann Oper Res, march 2017
