pp 58-64
Richa Singh
Research Scholar, Suresh GyanVihar University, Jaipur
richchauhan7@gmail.com
Manoj Kumar Sharma
Professor, Suresh GyanVihar University, Jaipur
manoj.sharma@mygyanvihar.com
Abstract: In the present technology for multimedia System, Wireless Network based Video Communication is an important point. As it is accepted, wireless channels often suffer from multipath attenuation, shadowing, inter-image interference, and so forth. P2P networking architectures receive a lot of attention today, as they enable a range of latest applications that may profit from the distributed storage and exaggerated computing resources offered by such networks. In addition, P2P systems represent a scalable and price effective various to classic media delivery services, which permits for extended network coverage in the absence of information science multicast or pricy Content Distribution Networks (CDNs). Their advantage resides in their ability for self-organization, bandwidth measurability, and network path redundancy, which area unit all terribly enticing options for effective delivery of media streams over networks.In this Research,we are improving the performance of the Video transmission without any error. We are working at Transmission Control Protocol (TCP) for reduce the Bit Error Rate (BER) of the system.
Keywords: Peer to Peer streaming, Video Streaming, QOS, Quality Adaptation, Active Measurement.
- INTRODUCTION
“The emergence of peer-to-peer computing signifies a revolution in connectivity that can be as profound to the net of the long run as Mosaic was to the net of the past”.
Although peer-to-peer networking has received a so much of attention recently thanks to the continuing battle with the music and screenland, it is not a brand new concept. In its simplest definition, peer-to-peer is described as [1]:
“A communications model in which every party has a similar capabilities and either party will initiate a communication session”. This means that conceptually, peer-to-peer computing may be an alternative to the standard shopper / server design wherever there usually is a single (or little cluster) server and lots of shoppers
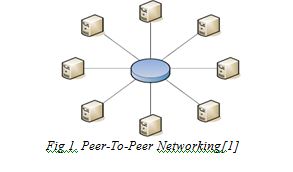
Sticking with the previous definition, the concept of peer-to-peer will be derived back to the 1960’s once the first implementation of the net (ARPANET) was a peer-to-peer network during which all its peers were equals. However, this definition can be fitted into several eventualities. The Domain Name System (DNS) may be a ideal of a mix between the standard peer-to-peer networking and a hierarchical model of data possession. A more precise definition is declared in [3] as:
“A distributed network architecture could also be known as a Peer-to-Peer (P-to-P, P2P,…) network, if the participants share a part of their own (hardware) resources (processing power, storage capacity, network link capacity, printers,…). These shared resources are necessary to give the Service and content offered by the network (e.g. file sharing or shared workspaces for collaboration).They are accessible by alternative peers directly, without passing go-between entities. The participants of such a network are therefore resource (Service and content) suppliers as well as resource (Service and content) requestors (Servant-concept).”
Fig 1. Peer-To-Peer Networking[1]
As there exists many forms of peer-to-peer networks, both with and without some with a form of central entity, this definition was further refined in [7]. This refinement introduced a classification of peer-to-peer networks as either pure (Figure 2) or hybrid (Figure 3). This was done so one is be able to distinguish between peer-to-peer networks with or without the previously mentioned central entity.
II. PEER-TO-PEER NETWORK TOPOLOGIES
A. Pure peer-to-peer
The “pure” peer-to-peer concept is a network in which the peers themselves are the only entities allowed .
“Distributed network architecture has to be classified as a “Pure” Peer-to-Peer network, if it is firstly a Peer-to-Peer network according to Definition 1 and secondly if any single, arbitrary chosen Terminal Entity can be removed from the network without having the network suffering any loss of network service.”
This is concept is showed in Figure 2. Here we can clearly see that only what seem to be equal peers are present in the network. All are interconnected which means that any peer can be removed, without this having any fatal consequences on the network, i.e. there is no single point of failure.

B. Hybrid peer-to-peer
Different from a “pure” peer-to-peer concept, where only the peers themselves were allowed in the network, a “hybrid” network will always include some sort of central entity. This is shown in Figure 3. In [17] the hybrid peer-to-peer concept is defined as:
“A distributed network architecture has to be classified as a “Hybrid” Peer-to-Peer network, if it is firstly a Peer-to-Peer network according to Definition 1 and secondly a central entity is necessary to provide parts of the offered network services.”
As Figure 3 shows, there are now hub nodes in the network which connects different networks. If one of these nodes go down, e.g. the center hub node of Figure 3, some parts of the network are suddenly separated. This makes the Hybrid peer-to-peer network more vulnerable to attacks or failure.
Fig 3. Hybrid peer-to-peer[1]

Peer-to-peer (P2P) is an alternative network model to that provided by traditional client-server architecture. P2P networks use a decentralized model in which each machine, referred to as a peer, functions as a client with its own layer of server functionality1. A peer plays the role of a client and a server at the same time. That is, the peer can initiate requests to other peers, and at the same time respond to incoming requests from other peers on the network. It differs from the traditional client-server model where a client can only send requests to a server and then wait for the server’s response. With a client-server approach, the performance of the server will deteriorate as the number of clients requesting services from the server increase. However, in P2P networks overall network performance actually improves as an increasing number of peers are added to the network. These peers can organize themselves into ad-hoc groups as they communicate, collaborate and share bandwidth with each other to complete the tasks at hand (e.g. file sharing). Each peer can upload and download at the same time, and in a process like this, new peers can join the group while old peers leave at any time. This dynamic re-organization of group peer members is transparent to end-users[22-28].
Another characteristic of a P2P network is its capability in terms of fault-tolerance. When a peer goes down or is disconnected from the network, the P2P application will continue by using other peers. For example, in a Bit Torrent system, any clients downloading a certain file are also serving as servers. When a client finds one of the peers is not responding, it searches for other peers, picks up parts of the file where the old peer was, and continues the download process. Compared to a client-server model, where all communication will stop if the server is down, a P2P network is more fault-tolerant.
C.Advantages Of Peer-To-Peer Networking
1) It is easy to install and so is the configuration of computers on this network,
2) All the resources and contents are shared by all the peers, unlike server-client architecture where Server shares all the contents and resources.
3) P2P is more reliable as central dependency is eliminated. Failure of one peer doesn’t affect the functioning of other peers. In case of Client –Server network, if server goes down whole network gets affected.
4) There is no need for full-time System Administrator. Every user is the administrator of his machine. User can control their shared resources.
5) The over-all cost of building and maintaining this type of network is comparatively very less.
- P2P VIDEO TRANSMISSION OVER MIMO-OFDM SYSTEM
Video communication over wireless network has been a significant challenge for current multimedia technology. As it is well known, wireless channels often suffer from multipath fading, shadowing, inter symbol interference, and so forth. Meanwhile, compressed video is very sensitive to error-prone environment. Any transmission error may lead to the loss of decoding synchronization and severe degradation to the received video quality.
Fortunately, great progresses have been made in the recent development of wireless communication and video transmission. Orthogonal frequency-division multiplexing (OFDM) has become a promising technique for transmission of signals in the broadband wireless communication systems. Moreover, multiple antennas system with multiple transmitters and multiple receivers, called a multiple-input and multiple-output (MIMO) system, has been shown to be an effective way to transmit high data rate over wireless channels. Therefore, OFDM in conjunction with multiple-input and multiple-output is not only able to enhance the capacity of system but also able to combat the channel fading and interference effectively[29-32].
It is widely believed that multiple-transmit and-receive antennas can improve the performance of wireless systems. Actually, this benefit can be exploited in two ways: spatial diversity and spatial multiplexing. Spatial diversity can im-prove the reliability of reception to combat channel fading by sending signals that carry the same information through independent paths. Such diversity schemes can be implemented using trellis-based space-time codes and orthogonal designs. For example, space-time block codes (STBCs) have been proposed to achieve diversity gains [1]. On the other hand, spatial multiplexing can provide higher data rate by transmitting different data streams in parallel through independent channels. Several schemes have been proposed to exploit the benefit of spatial multiplexing phenomenon. For ex-ample, Bell Labs space-time architecture (BLAST) [2] is such a scheme. In another words, multiple-transmit and-receive antennas can be used to provide higher reliability of reception using spatial diversity or give higher throughout using spatial multiplexing. In this paper, we will exploit the benefits from both types of these two schemes for robust P2P video transmission over wireless channels.
Meanwhile, in image and P2P video transmission applications, several approaches have been proposed to improve the robustness of image and P2P video transmission over error-prone network such as Internet and wireless network. Multiple-description coding (MDC) is such an effective source coding method. MDC generates multiple encoded bit streams that are equally important and independent. The objective of MDC is that if all bit streams have been received correctly, a high signal quality can be reconstructed, whereas, if some bit streams have been lost, a low-quality, but acceptable sig-nal quality can still be reconstructed from the received de-scription. MDC uses the idea of diversity to transmit bit-streams along different channels with the premise that each channel experiences independent failure events, such that the probability of receiving the information from each channel is equal. This assumption is also true in MIMO channel case. In a system with transmit and receive antennas, the channel between individual antenna pairs is assumed to be independent and identically distributed (i.i.d.). Moreover, the probability of all channels between antenna pairs falling into deep fading simultaneously is small. Therefore, MDC is also very suitable for robust P2P video transmission over multiple antennas system. There have been several works to report video trans-mission over multiple antennas system [3–7]. However, none of these existing schemes have explored the integration of data bit streams transmission using MDC and MIMO-OFDM. In this research, we construct a new system that integrates multiple-description coding, error-resilient video coding, unequal error protection scheme using hybrid space-time coding structure for robust video trans-mission over MIMO-OFDM system. In this paper, we pro-pose a multiple-description coding scheme based on wavelet video coding, where each generated description still retains the main quality of the original image. In the present of lost descriptions, we can perform error concealment method to compensate the lost descriptions without introducing some amount of redundancy between the descriptions. Unlike traditional multiple-description schemes, the proposed multiple-description algorithm enables us to generate more than two bit streams that may be more appropriate for multiple-antenna transmission of compressed video.

- TRANSMISSION CONTROL PROTOCOL(TCP)
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliable, ordered, and error-checked delivery of a stream of octets between applications running on hosts communicating by an IP network. Major Internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP. Applications that do not require reliable data stream service may use the User Datagram Protocol (UDP), which provides a connectionless datagram service that emphasizes reduced latency over reliability.
The Transmission Control Protocol provides a communication service at an intermediate level between an application program and the Internet Protocol. It provides host-to-host connectivity at the Transport Layer of the Internet model. An application does not need to know the particular mechanisms for sending data via a link to another host, such as the required packet fragmentation on the transmission medium. At the transport layer, the protocol handles all handshaking and transmission details and just presents an abstraction of the network connection to the application.
At the lower levels of the protocol stack, due to network congestion, traffic load balancing, or other unpredictable network behavior, IP packets may be lost, duplicated, or delivered out of order. TCP detects these problems, requests re-transmission of lost data, rearranges out-of-order data and even helps minimize network congestion to reduce the occurrence of the other problems. If the data still remains undelivered, its source is notified of this failure. Once the TCP receiver has reassembled the sequence of octets originally transmitted, it passes them to the receiving application. Thus, TCP abstracts the application’s communication from the underlying networking details.
TCP is used extensively by many applications available by internet, including the World Wide Web (WWW), E-mail, File Transfer Protocol, Secure Shell, peer-to-peer file sharing, and streaming media applications. TCP is optimized for accurate delivery rather than timely delivery. Therefore, TCP sometimes incurs relatively long delays (on the order of seconds) while waiting for out-of-order messages or re-transmissions of lost messages. It is not particularly suitable for real-time applications such as Voice over IP. For such applications, protocols like the Real-time Transport Protocol (RTP) operating over the User Datagram Protocol (UDP) are usually recommended instead.
TCP is a reliable stream delivery service which guarantees that all bytes received will be identical with bytes sent and in the correct order. Since packet transfer by many networks is not reliable, a technique known as ‘positive acknowledgement with re-transmission’ is used to guarantee reliability of packet transfers. This fundamental technique requires the receiver to respond with an acknowledgement message as it receives the data. The sender keeps a record of each packet it sends and maintains a timer from when the packet was sent. The sender re-transmits a packet if the timer expires before the message has been acknowledged. The timer is needed in case a packet gets lost or corrupted [33-34].
While IP handles actual delivery of the data, TCP keeps track of ‘segments’ – the individual units of data transmission that a message is divided into for efficient routing through the network. For example, when an HTML file is sent from a web server, the TCP software layer of that server divides the sequence of file octets into segments and forwards them individually to the IP software layer (Internet Layer). The Internet Layer encapsulates each TCP segment into an IP packet by adding a header that includes (among other data) the destination IP address. When the client program on the destination computer receives them, the TCP layer (Transport Layer) re-assembles the individual segments and ensures they are correctly ordered and error-free as it streams them to an application.
To establish a connection, TCP uses a three-way handshake. Before a client attempts to connect with a server, the server must first bind to and listen at a port to open it up for connections: this is called a passive open. Once the passive open is established, a client may initiate an active open. To establish a connection, the three-way (or 3-step) handshake occurs:
A.SYN
The active open is performed by the client sending a SYN to the server. The client sets the segment’s sequence number to a random value A.
B.SYN-ACK
In response, the server replies with a SYN-ACK. The acknowledgment number is set to one more than the received sequence number i.e. A+1, and the sequence number that the server chooses for the packet is another random number, B.
C.ACK
Finally, the client sends an ACK back to the server. The sequence number is set to the received acknowledgement value i.e. A+1, and the acknowledgement number is set to one more than the received sequence number i.e. B+1.
At this point, both the client and server have received an acknowledgment of the connection. The steps 1, 2 establish the connection parameter (sequence number) for one direction and it is acknowledged. The steps 2, 3 establish the connection parameter (sequence number) for the other direction and it is acknowledged. With these, a full-duplex communication is established.
D .Connection Termination
The connection termination phase uses a four-way handshake, with each side of the connection terminating independently.
When an endpoint wishes to stop its half of the connection, it transmits a FIN packet, which the other end acknowledges with an ACK. Therefore, a typical tear-down requires a pair of FIN and ACK segments from each TCP endpoint. After the side that sent the first FIN has responded with the final ACK, it waits for a timeout before finally closing the connection, during which time the local port is unavailable for new connections; this prevents confusion due to delayed packets being delivered during subsequent connections.

A connection can be “half-open”, in which case one side has terminated its end, but the other has not. The side that has terminated can no longer send any data into the connection, but the other side can. The terminating side should continue reading the data until the other side terminates as well.
It is also possible to terminate the connection by a 3-way handshake, when host A sends a FIN and host B replies with a FIN & ACK (merely combines 2 steps into one) and host A replies with an ACK.
Some host TCP stacks may implement a half-duplex close sequence, as Linux or HP-UX do. This allows a TCP application to be sure the remote application has read all the data the former sent—waiting the FIN from the remote side, when it actively closes the connection. But the remote TCP stack cannot distinguish between a Connection Aborting RST and Data Loss RST. Both cause the remote stack to lose all the data received.
RESULTS
In this section, we are showing the results of the P2P OFDM (Orthogonal Frequency Division Multiplexing) MIMO (Multiple Input Multiple Output) based Space-Time Coding methodology and propose d methodology P2p network based Transmission Control Protocol.

Figure 6 is showing the Video framer , which we have to transmit . In P2P network complete video will not transmit at a time . It divide into frames and then it transmit .

Figure 7 is showing the Comparison graph for the P2P OFDM (Orthogonal Frequency Division Multiplexing) MIMO (Multiple Input Multiple Output ) based Space-Time Coding methodology and proposed methodology P2P network based Transmission Control Protocol(TCP). As we can see from the figure 7 the Bit Error Rate(BER) is low for the proposed method P2P network based TCP protocol .
- CONCLUSION AND FUTURE SCOPE
- Conclusion
Peer-to-peer (P2P) systems are becoming increasingly popular due to their ability to deliver large amounts of data at a reduced deployment cost. While P2P systems foster the development of novel media applications, they also represent an interesting alternative paradigm for media streaming applications that can benefit from the inherent self organization and resource scalability available in such environments. In this research, we are working over P2P network for Video Transmission. For video transmission, we are working for reduce the BER (Bit Error Rate). In the base paper, they was working at robust P2P video transmission over MIMO-OFDM system to improve the robustness of signal source and adopting hybrid space-time coding structure to obtain unequal error protection during transmission. MIMO-OFDM is a promising technique for the broadband wireless communication system. In our Research , we are working for the P2P network based Transmission Control Protocol(TCP). Transmission control protocol is able to control the Bit Error Rate of the P2P network which are introducing at the Video Transmission.
- Future Scope
We consider the problem of real-time streaming of IP packet video over Peer-to-Peer networks (P2P) from multiple senders to a single receiver. P2P networks are characterized by a potentially large and highly dynamic population of hosts that join and leave the network frequently. We present the design and evaluation of a quality adaptation streaming mechanism in a multi-source streaming to a single receiver. In the Future ,we can further reduce the Bit Error Rate(BER) by User Datagram Protocol (UDP) in P2P Network.
REFERENCES
[1] V. Tarokh, H. Jafarkhani, and A. R. Calderbank, “Space-time block codes from orthogonal designs,” IEEE Transactions on Information Theory, vol. 45, no. 5, pp. 1456–1467, 1999.
[2] G. J. Foschini, “Layered space-time architecture for wireless communication in a fading environment when using multi-element antennas,” Bell Labs Technical Journal, vol. 1, no. 2,
- 41–59, 1996.
[3] H. Zheng and K. J. R. Liu, “Space-time diversity for multime-dia delivery over wireless channels,” in Proceedings of IEEE In-ternational Symposium on Circuits and Systems (ISCAS ’00), vol. 4, pp. 285–288, Geneva, Switzerland, May 2000.
[4] H. Zheng and D. Samardzija, “Performance evaluation of in-door wireless systems using BLAST testbed,” in Proceedings of IEEE Vehicular Technology Conference (VTC ’01), vol. 2, pp. 905–909, Atlantic City, NJ, USA, May 2001.
[5] Z. Ji, Q. Zhang, W. Zhu, Z. Guo, and J. Lu, “Power-efficient MPEG-4 FGS P2P video transmission over MIMO-OFDM sys-tems,” in Proceedings of IEEE International Conference on Com-munications (ICC ’03), vol. 5, pp. 3398–3402, Anchorage, Alaska, USA, May 2003.
[6] Z. Ji, Q. Zhang, W. Zhu, J. Lu, and Y.-Q. Zhang, “Video broad-casting over MIMO-OFDM systems,” in Proceedings of IEEE International Symposium on Circuits and Systems (ISCAS ’03), vol. 2, pp. 844–847, Bangkok, Thailand, May 2003.
[7] C.-H. Kuo, C.-S.Kim, and C.-C. J. Kuo, “Robust video trans-mission over wideband wireless channel using space-time coded OFDM systems,” in Proceedings of IEEE Wireless Com-munications and Networking Conference (WCNC ’02), vol. 2,
- 931–936, Orlando, Fla, USA, March 2002.
[8] D. W. Redmill and N. G. Kingsbury, “The EREC: an error-resilient technique for coding variable-length blocks of data,” IEEE Transactions on Image Processing, vol. 5, no. 4, pp. 565– 574, 1996.
[9] B.-J. Kim and W. A. Pearlman, “Embedded wavelet video coder using three-dimensional set partitioning in hierarchical trees (SPIHT),” in Proceedings of Data Compression Conference (DCC ’97), pp. 251–260, Snowbird, Utah, USA, March 1997.
[10] J. Liu and J. Li, “A simple soft-detector for the BLAST system,” in Proceedings of IEEE Sensor Array and Multichannel Signal Processing Workshop, pp. 159–163, Rosslyn, Va, USA, August 2002.
[11] Y. Andreopoulos, A. Munteanu, J. Barbarien, M. Van Der Schaar, J. Cornelis, and P. Schelkens, “In-band motion com-pensated temporal filtering,” Processing: Image Communica-tion, vol. 19, no. 7, pp. 653–673, 2004, special issue on Sub-band/Wavelet Interframe Video Coding.
[12] N. Franchi, M. Fumagalli, R. Lancini, and S. Tubaro, “Multiple description video coding for scalable and robust transmission over IP,” in Proceedings of the Packet Video Workshop (PV ’03), Nantes, France, April 2003.
[13] I. V. Bajic´ and J. W. Woods, “Domain-based multiple descrip-tion coding of images and video,” in Visual Communications and Image Processing, vol. 4671 of Proceedings of SPIE, pp. 124– 135, San Jose, Calif, USA, January 2002.
[14] A. C. Ashwin, K. R. Ramakrishnan, and S. H. Srinivasan, “Wavelet domain residual redundancy-based descriptions,” Signal Processing: Image Communication, vol. 18, no. 7, pp. 549–560, 2003.
[15] N. Tanabe and N. Farvardin, “Subband image coding using entropy-coded quantization over noisy channels,” IEEE Jour-nal of Selected Areas in Communications, vol. 10, no. 5, pp. 926– 943, 1992.
[16] J. M. Shapiro, “Embedded image coding using zerotrees of wavelet coefficients,” IEEE Transactions on Signal Processing, vol. 41, no. 12, pp. 3445–3462, 1993.
[17] A. Said and W. A. Pearlman, “A new, fast, and efficient im-age codec based on set partitioning in hierarchical trees,” IEEE Transactions on Circuits and Systems for Video Technol-ogy, vol. 6, no. 3, pp. 243–250, 1996.
[18] Y. Chen and W. A. Pearlman, “Three-dimensional subband coding of video using the zero-tree method,” in Visual Com-munications and Image Processing, vol. 2727 of Proceedings of SPIE, pp. 1302–1312, Orlando, Fla, USA, March 1996.
[19] L. Cao and C. W. Chen, “Robust image transmission based on wavelet tree coding, error resilient entropy coding, and error concealment,” Journal of Electronic Imaging, vol. 13, no. 3, pp. 646–653, 2004.
[20] C. Ru, L. Yin, and J. Lu, “An LDPC coded MIMO-OFDM sys-tem with simple detection and channel estimation scheme,” in Proceedings of the 6th IEEE Circuits and Systems Symposium on Emerging Technologies: Frontiers of Mobile and Wireless Com-munication, vol. 2, pp. 693–696, Shanghai, China, May-June 2004.
[21] “Digital Land Mobile Radio Communications – COST 207,” Commission of the European Communities, Final Report, Marzo 1984–Settembre 1988, Office for Official Publications of the European Communities, Luxembourg, 1989.
[22]. HaifengZheng, CongchongRu, Chang Wen Chen,andLun Yu,”P2P video transmission over MIMO-OFDM System: MDC and Space-Time Coding-Based Approaches “, Hindawi Publishing Corporation Advances in Multimedia Volume 2007.
[22] MK Sharma, Adaptive Steganographic Algorithm using Cryptographic Encryption RSA Algorithms Journal of Engineering, Computers & Applied Sciences (JEC& AS) 2 (1), 1-3, 2013.
[23] MK Sharma, Classification of image using a genetic general neural decision tree, Int. J. Applied Pattern Recognition 2 (1), 76, 2015.
[24] MK Sharma, An efficient segmentation technique for Devanagari offline handwritten scripts using the Feedforward Neural Network, Neural Computing and Applications 26 (2), 1-13, 2015.
[25] MK Sharma, Pixel plot and trace based segmentation method for bilingual handwritten scripts using feedforward neural network, Neural Computing and Applications 27 (7), 1817-1829, 2016.
[26] MK Sharma, Advanced Neuro-Fuzzy Approach for Social Media Mining Methods using Cloud, International Journal of Computer Applications (0975–8887) Volume 2, 2016.
[27] MK Sharma, Segmentation of english Offline handwritten cursive scripts using a feedforward neural network, Neural Computing and Applications, 1-11, 2015.
[28] MK Sharma, Offline scripting-free author identification based on speeded-up robust features, International Journal on Document Analysis and Recognition (IJDAR), Volume 18, Issue 4, pp 303–316, 2015.
[29] MK Sharma, Offline Language-free Writer Identification Based on Speeded-up Robust Features International Journal of Engineering (IJE), IJE TRANSACTIONS A: Basics 28 (7), 2015.
